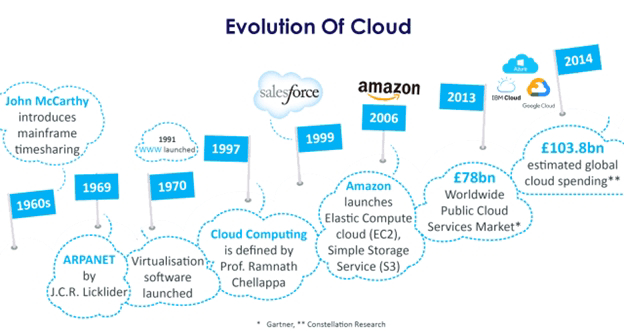
Brief description on SIEM (Security Information and Event Management)
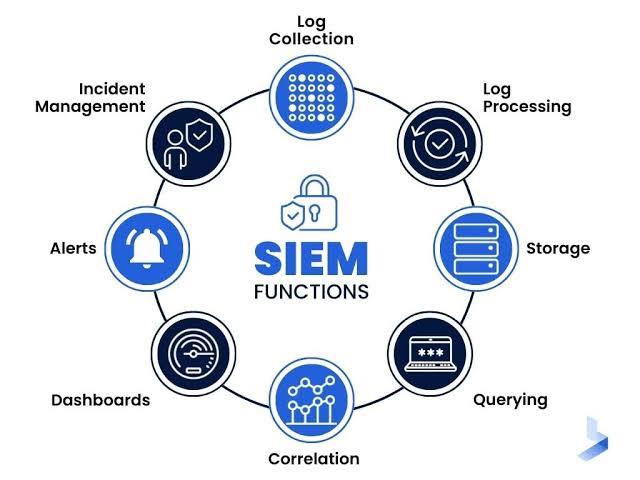
SIEM (Security Information and Event Management) tools are specialized software solutions that collect, analyze, and manage vast amounts of security data. They help security teams identify, investigate, and respond to security threats by monitoring events across an organization's network and systems. Key Features and Functions: Data Collection and Aggregation: SIEM tools gather log data, events, and other security-related information from various sources within the organization, such as firewalls, intrusion detection systems, servers, and applications. Real-time Monitoring and Analysis: They provide real-time visibility into security events and patterns, enabling security teams to quickly detect and respond to potential threats. Threat Detection and Alerting: SIEM solutions use rules and algorithms to identify suspicious activities and generate alerts, notifying security teams about potential security breaches. Incident Investigation and ...